The Synack platform expands to confront the cyber skills gap
https://cybersecureforum.co.uk/wp-content/uploads/2021/07/Synack-Logo-Lg.jpg 960 640 Guest Post Guest Post https://secure.gravatar.com/avatar/cb2a67f15cd7d053d8e638a1df3fd67f?s=96&d=mm&r=gBy Peter Blanks Chief Product Officer, Synack
At Synack, we’re committed to making the world a safer place. We’re doing that by helping organizations defend themselves against an onslaught of cyberattacks. We’re doing it by harnessing the tremendous power of the Synack Red Team, our community of the most skilled and trusted ethical hackers in the world, and through the most-advanced security tools available today.
Now, the Synack Platform is expanding to help organizations globally overcome the worldwide cybersecurity talent gap. I am excited to announce the launch of Synack Campaigns to provide on-demand access to the SRT, who will be available 24/7 to execute specific and unique cybersecurity tasks whenever you need them — and deliver results within hours. This new approach to executing targeted security operations tasks will fundamentally change organizations’ approach to cybersecurity by providing on-demand access to this highly skilled community of security researchers.
During my time at Synack, I’ve seen firsthand how the Synack Operations and Customer Success teams creatively engage with the SRT to address a growing range of clients’ security operations tasks, in addition to our traditional vulnerability discovery and penetration testing services.
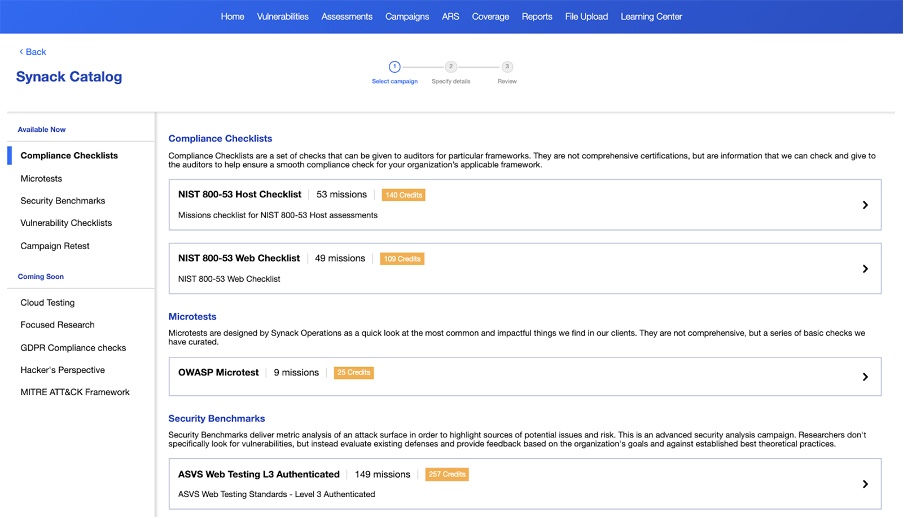
Now, we are making these targeted security activities directly available to every organization in the form of Synack Campaigns, available through the new Synack Catalog, also launching today on the Synack Client Platform.
The new Synack Catalog, where customers can discover, configure, purchase and launch Synack Campaigns is available now on the Synack Client Portal. Please speak with your CSM to have this feature enabled for your organization.
I know from speaking to our clients across multiple industries that security teams are struggling to keep pace with the speed of product development. At the same time, they are trying to scale defenses to meet the complexity and magnitude of today’s threats. Our customers ascribe challenges with their growing backlog of security tasks such as CVE checks and cloud configuration reviews. On top of all of that, there’s the need to implement industry best-practice frameworks such as OWASP & Mitre Att&ck. Essentially, customer security teams are struggling with demanding workloads and have asked us for assistance in a number of areas:
- On-demand access to talented Synack Red Team members who are available 24/7 and capable of completing diverse security operations activities across a growing range of assets.
- A flexible security solution that can be configured to meet their specific needs in one centralized platform with their existing pentesting insights.
- A security solution that delivers results quickly (hours and days, not weeks or months) and is aligned with their agile development processes.
Synack Campaigns expands the core capabilities of the Synack Platform, including our trusted community of researchers, an extensive set of workflows, payment services, secure access controls and intelligent skills-based task-routing to provide customers with the ability to execute a growing catalog of cybersecurity operations.
With Synack Campaigns our researchers can augment internal security teams by performing targeted security checks such as:
- CVE and OWASP Top 10 vulnerability checks
- Cloud Configuration Checks
- Compliance Testing (NIST, PCI, GDPR, etc.)
- ASVS Checks
Synack Campaigns are built to complement our vulnerability management and pentesting services, and help customers achieve long-term security objectives, such as Application Security, M&A Due Diligence, and Vulnerability Management.