Geopolitical risk ‘will provide CIOs with new leadership opportunities’
https://cybersecureforum.co.uk/wp-content/uploads/2022/09/Cyber-security-image-2.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gTechnology governance issues emanating from cross-country politics have led to digital geopolitics rapidly becoming an issue that multinational CIOs must step up to lead, according to Gartner.
Forty-one percent of Boards of Directors view geopolitical power shifts and turbulence as one of the biggest risks to performance, according to a Gartner survey. Gartner predicts that by 2026, 70% of multinational enterprises will adjust the countries in which they operate by hedging to reduce their geopolitical exposure.
“Digital geopolitics is now one of the most disruptive trends that CIOs must address, with many now dealing with trade disputes, legislation coming from one country that impacts global operations, and government imposed restrictions on the acquisition and use of digital technology,” said Brian Prentice, VP analyst and Gartner Fellow. “They need to get acquainted with this new reality and prepare for its impact.”
Geopolitics describes the geographic influences on power relationships in international relations. The resulting competition between nations plays out in many areas, including economic, military and society. Due to the increasing importance that digital technology plays in each of these areas, digital geopolitics is emerging as its own unique category of impact.
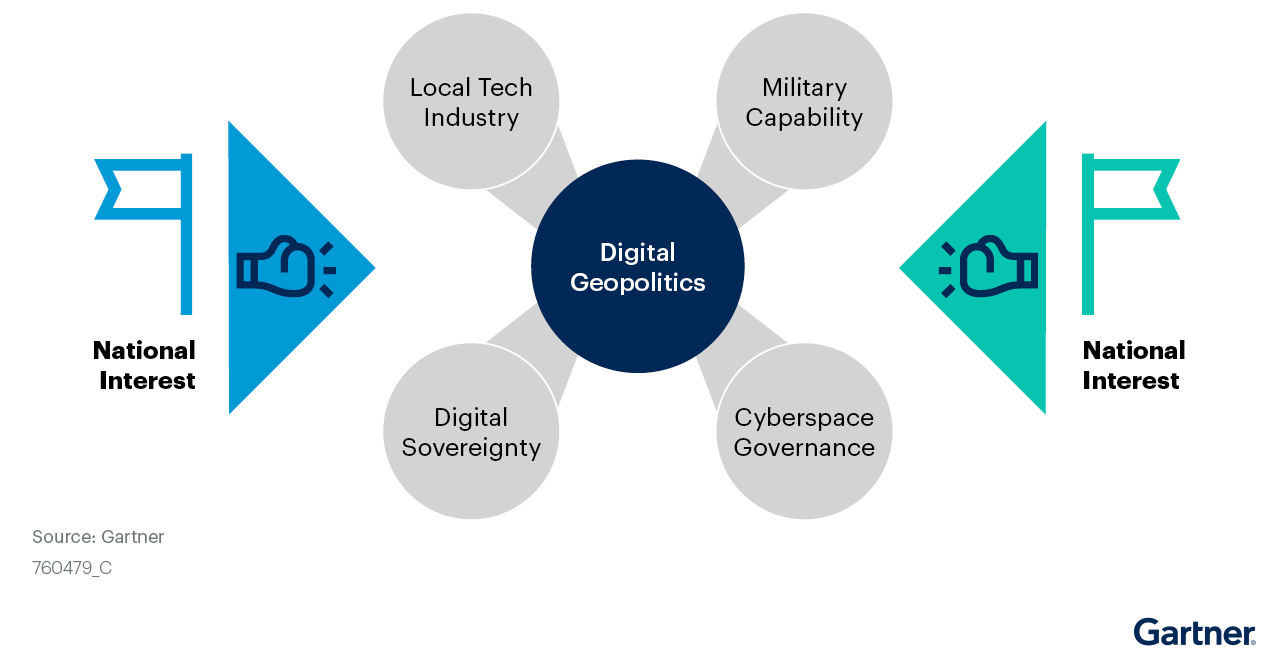
Gartner says CIOs must play a pivotal role in assessing corporate risk and, if required, rearchitecting digital systems. They will need to manage or exploit four distinct facets of digital geopolitics (see graphic below).
1. Protect digital sovereignty
Digital sovereignty will be a primary source of complex, dynamic and expanding compliance obligations for multinational enterprises. Governments are primarily addressing it through their legislative and regulatory powers, such as privacy laws like the GDPR, and are increasingly turning to extraterritorial legislation. Companies that deal with the citizens of a jurisdiction are required to comply with its laws, regardless of where the company operates or where the citizens reside.
CIOs must be proactively engaged in ensuring that the IT organization’s operating model and practices reflect current laws and regulations in place. Their role is to be aware of the legal environment and articulate to other executives how the IT organization supports compliance across the enterprise.
2. Build a local technology industry
The technology industry is of great interest to public policymakers around the world due to its size, fast growth, strategic importance, tax revenue, employment possibilities and lack of requirement for a specific national resource advantage.
Many national governments are investing in developing a home-grown tech sector. For example, the U.S. seeks to address regional imbalance in global chip production through the Creating Helpful Incentives to Produce Semiconductors (CHIPS) for America Act, and the Australian Government’s Digital Economy Strategy 2030 includes building a dynamic and emerging tech sector as a key pillar.
Efforts to establish a domestic technology industry provide CIOs with an opportunity for proactive engagement with governments. They must localize specific initiatives into countries that have the best integration between local expertise and access to government co-innovation support.
3. Achieve necessary military capability
The growing digitalization of national military and security operations will limit the availability of some technologies within various countries. Enterprises and CIOs are impacted by the emerging sphere of cyberwarfare, as well as the digitalization of existing warfighting and security technologies.
CIOs can no longer count on the availability of technology used by the enterprise for its operations in any country in which it operates and will likely be faced with restricted and mandated suppliers. To minimize disruptions, they must establish a vendor and technology risk center of excellence, chartered with a regular assessment of the exposure of key suppliers to evolving government restrictions.
4. Exert direct control over the governance of cyberspace
National competition for control over the governance of cyberspace will impact the operations of multinational enterprises. As digital technology weaves itself through all aspects of society, nations are seeking to ensure that their own technologies reflect and support their core values and their citizens. Governments are increasingly concluding that they need a protected national digital infrastructure.
The machinations by governments for control over cyberspace governance are beyond the influence of CIOs, but they will have profound impacts on a business’ ability to operate internationally. CIOs can advance the executive team’s understanding of cross-national competition for control over cyberspace and the impacts to their enterprise’s operations by leading an annual cyberspace environmental update briefing.