How to combat cyber organised crime with XDR
https://cybersecureforum.co.uk/wp-content/uploads/2022/01/Security-HQ-Jan-27th-2.jpg 960 640 Eleanor Barlow Eleanor Barlow https://cybersecureforum.co.uk/wp-content/uploads/2022/03/Ellie-170--96x96.jpgAccording to Verizon’s latest ‘2021 Data Breach Investigations Report (DBIR)’, in the past few years, financially motivated attacks continue to be the most common forms of attacks, with organized crime groups representing around 80% of these attacks.
In fact, in a threat assessment delivered by Europol, a warning was released stating the frightful impact that criminal syndicates are having on the economy. The assessment highlighted that ‘Virtually all criminal activities now feature some online components, such as digital solutions facilitating criminal communications’, and that ‘The availability and accessibility of secure online channels has resulted in a diversification of the platforms used for illegal online trade.’
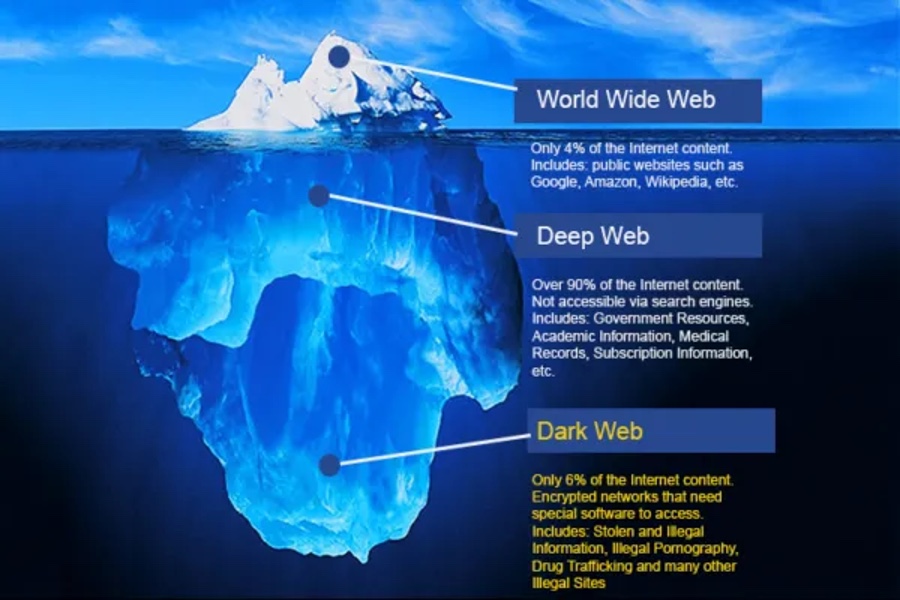
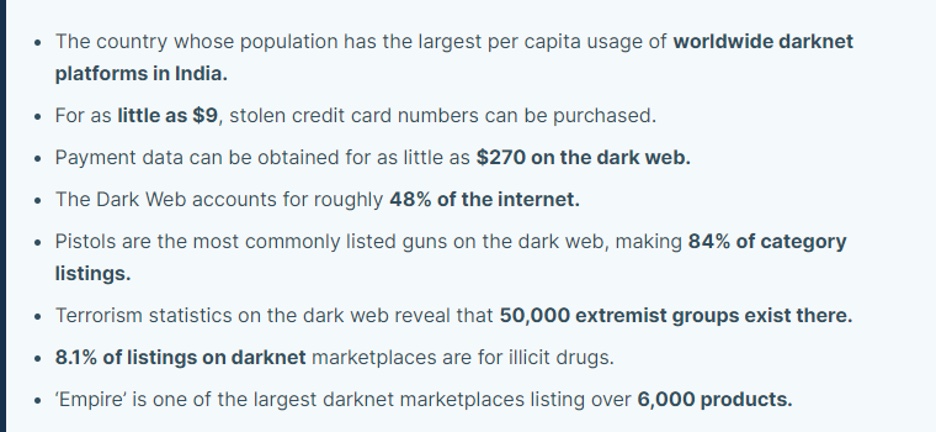
The Dark Web for Criminal Communication
The Surface Web and the Dark Web is a breeding ground for organised crime groups. ‘There are organised crime groups such as drug dealers, arms dealers, and other general criminal activities. There are also hacking groups, trading information, selling ransomware, credit cards and so forth. But, apart from acting as a marketplace, the Dark Web also acts as a communication for said parties. When you couple it with the anonymous payment of cryptocurrency, such as Bitcoin, you’re in business. You have the means to communicate with likeminded individuals, you have customers ready to buy, and a payment mechanism. Which is the dream scenario for anyone wanting to stay below the radar.’ – Eleanor Barlow, SecurityHQ
Cybercrime delivered as a service is also highly sought after and provides those with lesser skills to be able to commit illegal actions, including DDoS attacks, ransomware, and fraud. Tools can be purchased using a percentage of the criminal profits, and there are multiple manuals and how-to guides available for wannabe threat actors to start attacks.
XDR to Combat and Mitigate against Cyber Organised Crime
To keep up with growing organised crime threats, businesses now require different combinations of detection and response capabilities. SecurityHQ offers Extended Detection & Response (XDR) with multiple feature options, to ensure an enhanced security posture. By combining Network Detection and Response, Endpoint Detection and Response, SIEM, User Behaviour Analytics, and 24/7 SOC capabilities for real-time Detection and Active Response, receive 360-degree visibility that is constantly evolving and adapting to your hybrid, multi-cloud, IT environment, across your logs, Endpoint, and network, to increase speed of detection and remediation of both known and unknown threats.
For more information on how to mitigate against cyber organised crime, talk to a SecurityHQ expert.