How to mitigate non-malicious insider risk (and why employee awareness is key)
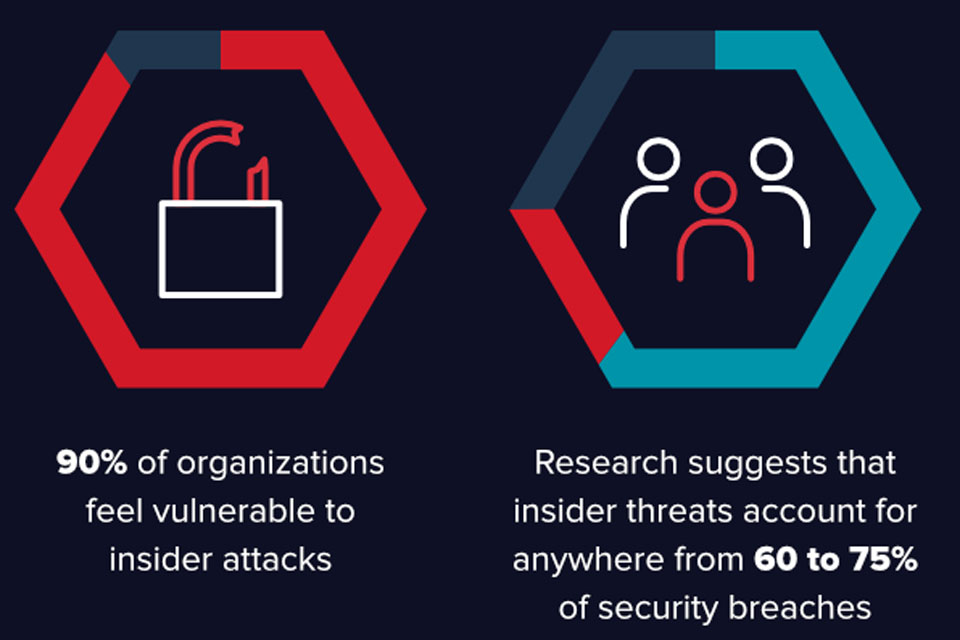
https://cybersecureforum.co.uk/wp-content/uploads/2021/10/infosecurity.jpg 960 640 Guest Post Guest Post https://secure.gravatar.com/avatar/cb2a67f15cd7d053d8e638a1df3fd67f?s=96&d=mm&r=g‘Your people are your most important asset’ is a well-worn phrase. However, in the wrong environment, employees can also present a substantial cyber-threat to organizations, and evidence suggests this problem keeps on growing: there’s been a 47% rise in the frequency of incidents involving insider threats between 2018 and 2020, with over half (62%) of these incidents being non-malicious.
In this article, Infosecurity Magazine looks at what organizations can do to mitigate the rise of insider threat incidents, and the central role employee security awareness campaigns plays in guarding against this issue.