Microsoft
ManagedXDR Combines Talent and Technology to Deal with Microsoft Exchange Threat
https://cybersecureforum.co.uk/wp-content/uploads/2019/07/Barracuda-Email.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gBy Carolyn Reuss, director, product management at Secureworks & Pierre-David Oriol, senior consultant, product management at Secureworks
The explosion of data and devices is expanding the attack surface from the core to the edge. Cyber threats continue to rise, and cybercrime continues to accelerate. To achieve better security outcomes, security administrators need broad visibility across multiple sources and over time, to identify unknown threats.
The following outlines how Secureworks’ ManagedXDR coupled with Incident Response, detected malicious activity as Microsoft Exchange servers attempted to run a version of China Chopper web shell.
The most effective cyber defenses combine talent and technology. The two are not mutually exclusive. As the integrated response to this particular incident will demonstrate.
Early Monday, March 1, Secureworks Security Operations Center (SOC) analysts contacted the Secureworks Counter Threat Unit (CTU) researchers to report that Secureworks Taegis XDR (Extended Detection and Response) detected malicious activity via its endpoint telemetry across several customers as Microsoft Exchange servers attempted to run a version of China Chopper web shell.
Initial Response and Findings
The SOC’s note initiated a routine response, engaging CTU researchers, Incident Response (IR) Teams, and engineers to collect critical, relevant intelligence such as initial attack vector, attack failures and successes, impacted customers (by looking back over a year’s worth of event data), and importantly, understanding the intent. This demonstrates that while XDR’s detection capabilities stand on its own for an individual instance, ManagedXDR working in concert with other systems and human resources amplifies the “network effect” when observing an event that impacts multiple organisations, and the whole XDR community benefits.
In this event, endpoint telemetry was critical to detecting and understanding the threat. Looking across customers’ endpoint telemetry, the team identified related intrusion activity across the affected businesses.
The next day, once we had a comprehensive understanding of the threat, we released CTU TIPS to inform customers of the targeted campaign and provide initial recommendations. This was followed by automated XDR notifications about the threat at log-in. Additionally, Microsoft released out-of-band patches for on-premises Microsoft Exchange Servers that organisations with vulnerable systems needed to apply ASAP.
Dealing with Vulnerabilities
Vulnerability management is another vital element to this coordinated detection and response. Secureworks Taegis VDR (Vulnerability Detection and Response) helped affected businesses quickly identify and prioritise vulnerabilities in their environment. In this case, we automatically factored in specific vulnerabilities heightened by recent incidents and public interest into VDR, and delivered detections for CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065 as details about this vulnerability continued to surface.
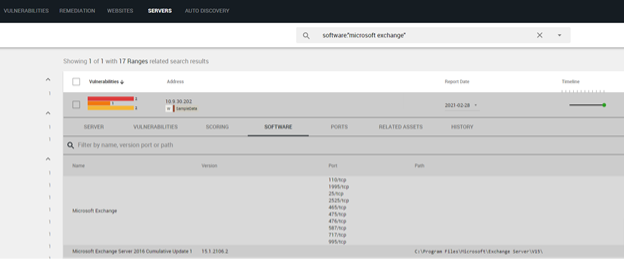
VDR provides businesses with the ability to search specifically for certain software (e.g., <software:“Microsoft Exchange”>) to accelerate their VM cycle outside of their regular scans and identify existing vulnerable assets. The contextual prioritisation engine allows businesses to easily identify which vulnerabilities create the highest risk in their environment. That risk is always subject to each organisation’s internal context, from which VDR continuously learns.
In this case, as the attack was exploiting unpatched on-premises Exchange Server versions 2013, 2016, and 2019, as such, VDR helped those organisations that were impacted to understand which of the occurrences of the above CVEs to address first, saving security experts critical triaging time. Businesses can either search specifically for Microsoft Exchange, (as shown above), or work from reliable detections for these CVEs, to confirm the finding is, or is not, a priority in comparison to other vulnerabilities within their environment.
Incident Response & Engagement Support
Working in tandem with their other colleagues, the IR team immediately started working with customers who had seen exploitation of their Microsoft Exchange servers from this activity, providing guidance on the remediation steps and identifying any further activity.
Additional Steps You Can Take
The threat is still live, so we recommend the following steps, if applicable, to keep your organisation safe:
- If you have on-premises versions of Exchange with the vulnerability, and you have concerns, invoke your incident response, whether it’s through our team, internally or through your Managed Security Services Provider (MSSP), to investigate whether access has been leveraged by the threat actor that Microsoft is currently referring to as HAFNIUM.
- Organisations using affected on-premises versions of Exchange Server should apply updates immediately, if possible. Please note that Exchange Online is not affected.
- Organisations should also closely monitor Exchange Server logs for relevant threat indicators, ensure a good EDR product to detect behaviors and apply indicators (e.g., Secureworks endpoint agent or one of our endpoint partners), and consider restricting access to the Microsoft Exchange Control Panel (ECP).
- If you are an existing VDR customer: Search for <software“Microsoft Exchange”> for a specific scan and continue to prioritise the highest risk in your environment.
Google, Microsoft back UK government on cyber security
https://cybersecureforum.co.uk/wp-content/uploads/2019/07/UK-Government.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gMajor businesses including Google and Microsoft have pledged to help the UK tackle the most damaging cyber security threats.
Up to £117 million of private industry investment will be combined with £70 million of government funding through the modern Industrial Strategy to develop new technologies.
These will range from a new and secure hardware prototype that can cope with cyber-attacks, to software protected from new vulnerabilities appearing online.
The government says that with cyber threats constantly evolving, the best defence in the future is seen as developing innovative solutions that can work independently and protect against threats even during attacks. It also wants to ensure that every UK organisation is as cyber secure and resilient as possible.
Nearly all UK businesses are reliant on digital technology and online services, yet more than 30% have experienced a cyber-security breach or attack in the last 12 months, according to the government’s own data.
For example, hackable home wifi routers can be used by attackers in botnets to attack major services and businesses.
The government says businesses are having to spend increasing amounts on cyber security, up to 20 to 40% of their IT spend in some cases. And as more and more systems are connected, whether in the home or businesses, there is a need for security that is secure by design.
Business Secretary Greg Clark said: “Digital devices and online services are powering more of our daily lives than ever before, from booking a doctors’ appointment to buying online shopping. While these devices and services bring great benefits to businesses and consumers, they come with the associated risks of cyber-attacks and threats that are becoming increasingly complex to tackle.
“As we move to a more data-driven economy, nearly all UK businesses and organisations are reliant on these digital technologies and online services – but the threat of cyber-attacks is ever-present, with more than 30% of businesses having experienced a cyber-security breach or attack in the last 12 months.
“With government and industry investing together as part of our modern Industrial Strategy, we will ensure that the UK is well placed to capitalise on our status as one of the world leaders in cyber security by ‘designing in’ innovative measures into our technology that protect us from cyber threats. This will also help us bring down the growing cybersecurity costs to businesses.”
This expected joint investment will create projects to develop new solutions to cyber security over the next 5 years, with the aim of applying the findings in real-world markets through dedicated demo-projects led by business.
For example, these demo projects could include testing the new technology in the health sector to ensure a higher level of protection for patient data, or in consumer markets to ensure consumers’ personal data is fully protected as far as possible.
Dr Ian Levy, National Cyber Security Centre’s Technical Director said: “The National Cyber Security Centre is committed to improving security from the ground up, and we have been working closely with government to promote adoption of technology and practices to protect the UK.
“We hope this additional investment will drive fundamental changes to products we use every day. This is vital work, because improving hardware can eradicate a wide range of vulnerabilities that cause significant harm.”
Developing innovative solutions to cyber security will help put the UK at the forefront of the AI and data revolution, in support of the government’s AI and Data Grand Challenge.
Details on the upcoming rounds of funding for this Digital Security by Design challenge, which will likely bring together academics, research institutions, start-ups, SMEs and large businesses, will be announced later this year.
Image by Gerd Altmann from Pixabay
WEBINAR: 6 Critical Steps for Securing Office 365, Thursday 9th May at 10am BST
https://cybersecureforum.co.uk/wp-content/uploads/2019/04/Everycloud-Webinar.jpg 960 640 Guest Post Guest Post https://secure.gravatar.com/avatar/cb2a67f15cd7d053d8e638a1df3fd67f?s=96&d=mm&r=gMicrosoft Office 365 continues to be the most used cloud-based application adopted by organisations worldwide. As a popular productivity suite, its capabilities are broad and help users collaborate with people both inside and outside their organisation.
A broad set of capabilities, however, creates challenges in accessing and protecting the data that is used across the various Office 365 applications, including SharePoint, OneDrive, Outlook, and Yammer. How can you effectively secure and govern data usage across these applications?
This webinar will highlight 6 important steps needed to better protect your data within Office 365.
Watch this webinar and learn more about:
· How to get real time visibility and control of risky activities across dozens of apps in Office 365
· How to protect your data from inside and outside threats
· How to protect your data while enabling multiple access methods (i.e. web, desktop app, managed / unmanaged device)
· How to ensure best practices and industry compliance
REGISTER HERE
Free Download – Microsoft Office 365 Security Whitepaper
Microsoft customers have options when it comes to Office 365 security controls—with varying coverage depending on their license level. But securing the Office 365 suite of cloud services is a shared responsibility between the cloud provider (Microsoft) and the customer.
If you want to find out how EveryCloud in partnership with Netskope can help Secure your Cloud Applications and help you to understand risky activity, protect and prevent against the loss of sensitive data and guard against cloud-based threats such as malware and ransomware.
Warning for businesses still using Windows 7
https://cybersecureforum.co.uk/wp-content/uploads/2019/01/Windows-7.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gThere’s just one year to go until Microsoft ends support for its ten-year-old operating system Windows 7, but as many as 43% of enterprises are still running the outdated platform.
That’s according to a new ‘Death of Windows 7’ report from Kollective.
The report, which includes data from a survey of 260 US and UK IT professionals, examines the potential costs and security threats involved in staying on Windows 7 after Microsoft’s support deadline passes.
Kollective’s research found that nearly a fifth (17%) of IT departments don’t know when the end of support deadline is, while 6% are aware of the end of support but are yet to start planning for their migration away from Windows 7.
Those that remain on Windows 7 past January 14, 2020 will either have to pay Microsoft significant sums for extended support or will leave their systems open to cyberattack. In the case of those largest enterprises, with 10,000 or more terminals, the fee to Microsoft could be in excess of $1.4m a year.
Perhaps most worrying of all, 16% of IT professionals admit to still running Windows XP and Windows Vista on some of their machines – despite support for these operating systems having ended more than three years ago.
Dan Vetras, CEO of Kollective, said: “With only a year to go, these findings should be a major cause for concern among the business community. When it came to migrating away from Windows XP it took some large enterprises as long as three years to transfer their entire systems to the new operating system, now, many firms will have to make the transition in less than 12 months. Those that fail to do so will have to pay for extended support, with the largest organizations paying more than a million dollars a year in order to remain on Windows 7.”
“Most worrying of all is that this migration is just the first step. Once businesses are on Windows 10, they will need to continuously update their systems as part of Microsoft’s new ‘Windows as a Service’ model. This means distributing increasingly frequent updates across their systems – something many IT departments will find impossible due to outdated infrastructure. At Kollective, we’re committed to raising awareness for this issue and helping enterprises solve their network challenges before it’s too late.”
Barracuda integrates with Microsoft Azure Virtual WAN
https://cybersecureforum.co.uk/wp-content/uploads/2018/09/barracuda-logo.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gMicrosoft launches identity bug program
https://cybersecureforum.co.uk/wp-content/uploads/2018/07/Microsoft.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gMicrosoft has unveiled a new bug program that rewards researchers for discovering vulnerabilities in Microsoft’s Identity services up to $100,000.
Rewards offered range from $500 to $100,000 for any flaws found that impact a range of services, including Microsoft and Azure Active Directory accounts, OpenID and OAuth 2.0 standards, Microsoft Authenticator applications for iOS and Android and identity services.
On a page dedicated to the new bug program, Microsoft invites security researchers who may have discovered a security vulnerability the opportunity to disclose of the problem privately to the company so they have the opportunity to fix the issue before publishing technical details, stating that “together we can bring assurance that digital identities are safe and secure.”
Microsoft goes on to say that “a high-quality report provides the information necessary for an engineer to quickly reproduce, understand, and fix the issue. This typically includes a concise write up containing any required background information, a description of the bug, and a proof of concept. We recognise that some issues are extremely difficult to reproduce and understand, and this will be considered when adjudicating the quality of a submission.”
A full description of the program can be found here.
NHS Digital signs cyber security contract with Microsoft
https://cybersecureforum.co.uk/wp-content/uploads/2017/08/nhs-logo-880x4951.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/9defd7b64b55280442ad2d7fb546a9db?s=96&d=mm&r=gNHS Digital has signed a support contract with Microsoft, three months after the WannaCry ransomeware attacks that targeted Windows computers.
The attacks on the NHS highlighted the need for investment, lack of infrastructure and the need for training among NHS staff, along with the fact that the NHS relies on Windows XP, an obsolete operating system that raised questions about the resilience of the service’s IT systems.
The Government recently announced it would boost investment in NHS data and cyber security above the £50 million outlined in the Spending Review, addressing key structural weaknesses as part of its commitment to improve NHS cyber security, with an initial £21 million delivered to increase cyber security at major trauma sites as a priority, along with improvement of NHS Digital’s national monitoring and response capabilities.
The support contract with Microsoft will cover all NHS organisations throughout the UK until June 2018 and provide a “centralised, managed and coordinated framework for the detection of malicious cyber activity through its enterprise threat detection software.”
A statement by the NHS added that the service “analyses intelligence and aims to reduce the likelihood and impact of security breaches or malware infection across the NHS.”
“One of NHS Digital’s key roles is to work closely with other national partners to explore and provide additional layers of cyber security support to NHS organisations when they need it – with the aim of minimising disruption to NHS services and patients,” the statement concluded.








