WEBINAR: Live Attack Simulation – Ransomware
https://cybersecureforum.co.uk/wp-content/uploads/2021/03/cybereason-1.png 553 289 Guest Post Guest Post https://secure.gravatar.com/avatar/cb2a67f15cd7d053d8e638a1df3fd67f?s=96&d=mm&r=gWednesday, March 24th @10:00 GMT
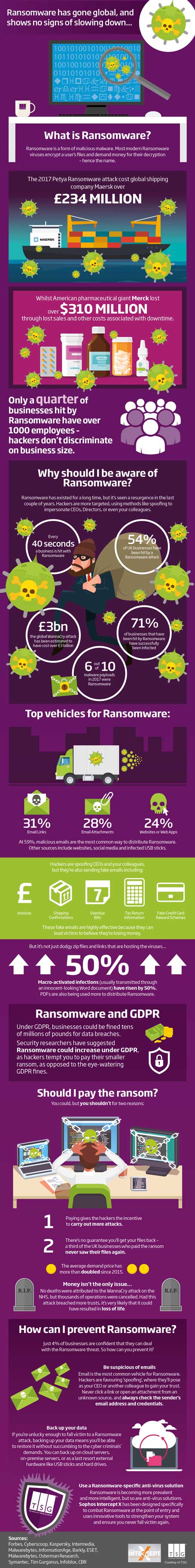
If you’re concerned about ransomware, whether it’s beating Ryuk, stopping data exfiltration, or preventing the latest trend of “double extortion”, this session is for you. Join Cybereason for a live attack simulation, where we’ll discuss the latest ransomware trends, walk through a multi-stage attack, and show the side by side Defenders view.
Beating modern ransomware attacks means not only preventing the ransomware from running, but finding and stopping the malicious behaviors that come before it. Our Nocturnus team researches every major strain of ransomware to continually improve our multi-layer prevention and our behavioural approach to threat detection with the Malop.
See our latest findings and why Cybereason arms you with fearless protection against ransomware to reduce risk across your enterprise.
Join us to learn:
– Why ransomware continues to evolve and common delivery methods
– How ransomware is used as the “last step” in kill chains
– See tactics and techniques used by FIN6 & UNC threat actors