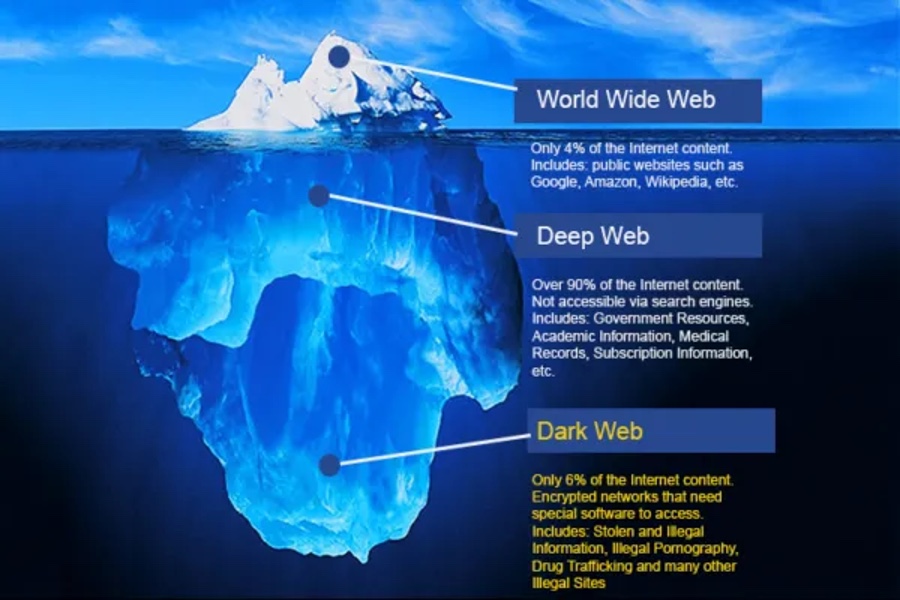
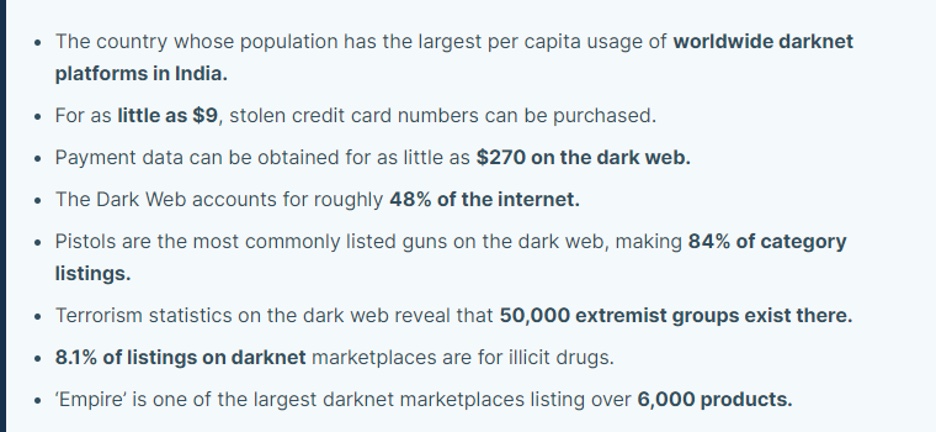
Cybersecurity insurance market ‘worth $29.2bn by 2027’
https://cybersecureforum.co.uk/wp-content/uploads/2022/07/insurance-calculator-385506_1280.jpg 960 640 Stuart O'Brien Stuart O'Brien https://secure.gravatar.com/avatar/81af0597d5c9bfe2231f1397b411745a?s=96&d=mm&r=gThe global Cybersecurity Insurance Market size in the post-COVID-19 scenario is projected to grow from $11.9 billion in 2022 to $29.2 billion by 2027, equivalent to a CAGR of 19.6% during the forecast period.
The report by ResearchAndMarkets says SMEs are majorly adopting cybersecurity insurance solutions and services to secure from cyberattacks and due to the growing instances of fraud.
It cites the insurance enterprise, Beazley, revealing that 60% of ransomware attacks were targeted toward SMEs, while Emsisoft, an anti-virus software firm, stated that businesses paid a ransom of $1.3 billion to cyberattackers in 2019.
SMEs are more vulnerable to cyberattacks as it is easier to gain access to their servers than larger networks, the report says. SMEs are expected to earmark more budgets for cybersecurity insurance in the coming years due to the soaring cases of cyber-induced attacks and the increasing mandatory legislation during the pandemic.
Asia Pacific countries are highly concerned about the increase in security spending due to the ever-growing threat landscape. For the report, the region comprises emerging economies, such as China, Japan, ANZ, and Singapore.
With effective government regulations and technological advancements, cybersecurity insurance is witnessing high growth opportunities in this region. Various developments are taking place in Asia Pacific, concerning the adoption of technologies, such as BI tools, cloud, analytics, and rapid infrastructure development.
The reports says an increase in regulatory developments, with surge in fines and penalties from non-compliance, is expected to uptake the demand for the Cybersecurity Insurance Market in Asia Pacific in the future.
For example, Zurich Insurance stated that the Cybersecurity Insurance Market is set to grow significantly in Asia Pacific. AIG, Allianz, Chubb, and Zurich are among the prominent players for cybersecurity insurance in the region currently