ContiLeaks: Ransomware gang suffers data breach
https://cybersecureforum.co.uk/wp-content/uploads/2022/03/Varonis-Mar-24th.jpg 960 640 Guest Post Guest Post https://secure.gravatar.com/avatar/cb2a67f15cd7d053d8e638a1df3fd67f?s=96&d=mm&r=gBy Varonis
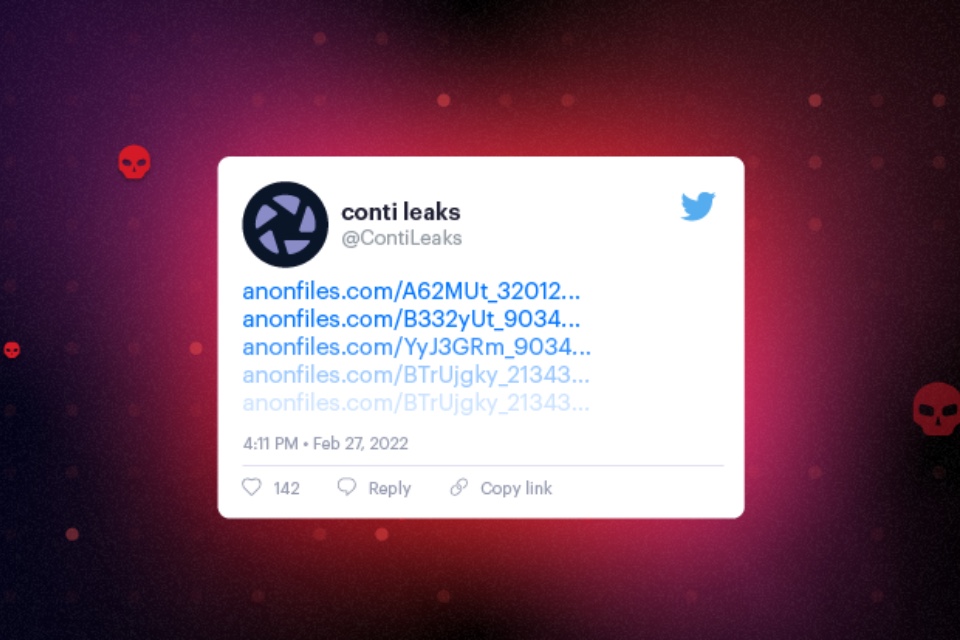
Conti, one of the most infamous, prolific and successful big game ransomware threats, has suffered yet another embarrassing leak with a treasure trove of both internal chat transcripts and source code being shared by a reported Ukrainian member.
Having previously had their internal manuals and tools exposed by a disgruntled affiliate in August 2021, these latest leaks appear to be in response to the group “officially announcing a full support of Russian government” [sic] and that they would respond to any attack, cyber or otherwise, against Russia with “all possible resources to strike back at the critical infrastructures of an enemy”.
Given that members of the group may themselves be Ukrainian or have close ties to the country, this warning likely inflamed tempers leading to both the warning being updated and these subsequent leaks.
Much as the previous leak allowed their toolsets to be analyzed and revealed common indicators of compromise (IOC), analysis of these recent data leaks and chat logs provides insights into how Conti, and likely other similar ransomware groups, coordinate and conduct their operations.
The outcome of these leaks remains to be seen; Conti and its members may be forced to disband or, as is often the case with ransomware groups, lay low for a period before rebranding and relaunching their operation.
Click here to finish reading the full blog post or visit the Varonis website here.