Say goodbye to traditional security training: How to keep your staff engaged!
https://cybersecureforum.co.uk/wp-content/uploads/2023/03/KnowBe4.jpg 960 640 Guest Post Guest Post https://secure.gravatar.com/avatar/cb2a67f15cd7d053d8e638a1df3fd67f?s=96&d=mm&r=gAs the saying goes, what got you here, won’t get you there. While the traditional method of once-a-year security awareness training for your staff may have been an acceptable method in the early 2000’s, times change, and so do the needs of staff. Simply providing information to employees is not enough. For best results, information delivered needs to be relevant, timely, and appropriate.
Take the example of teaching a child to cross the road. The best time to teach them is when you’re at a road. This makes the lesson timely and relevant. It also needs to be explained to them in terms they will understand and connect to, this makes it appropriate.
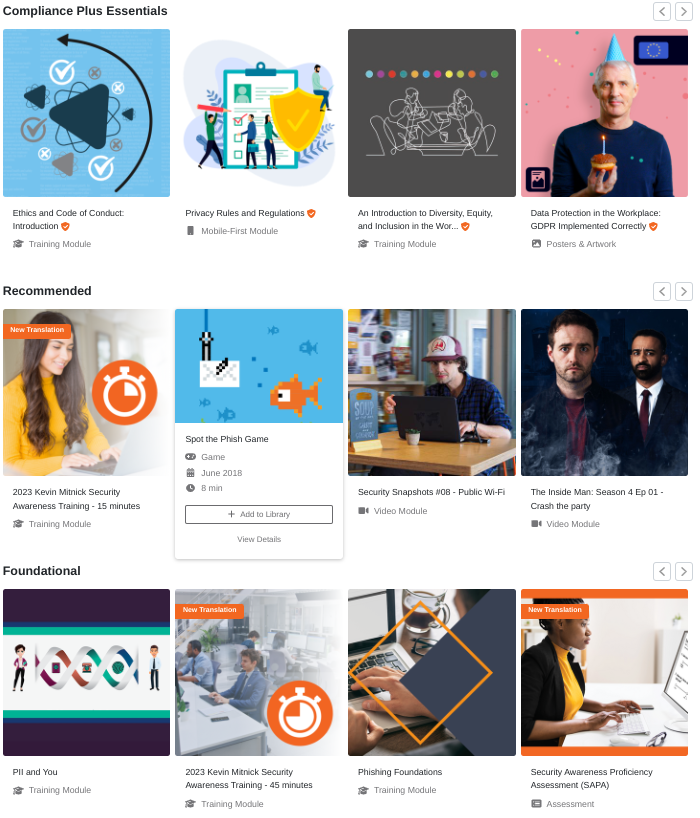 With KnowBe4, you can deliver training to employees which is relevant, timely, and appropriate. It contains a huge library of content covering training modules, video modules, mobile optimised content, assessments, games, newsletters, posters, and much more. Plus, the content is localised in many languages and with many different tones and formats available, there is certainly something for every organisation.
With KnowBe4, you can deliver training to employees which is relevant, timely, and appropriate. It contains a huge library of content covering training modules, video modules, mobile optimised content, assessments, games, newsletters, posters, and much more. Plus, the content is localised in many languages and with many different tones and formats available, there is certainly something for every organisation.
Smart groups can also be used to deliver specific training to selected users. For example, there is no point in making everyone go through security awareness tips when travelling, if most people never travel to a remote location. Putting your road warrior employees in one group and only sending them the training makes it far more relevant.
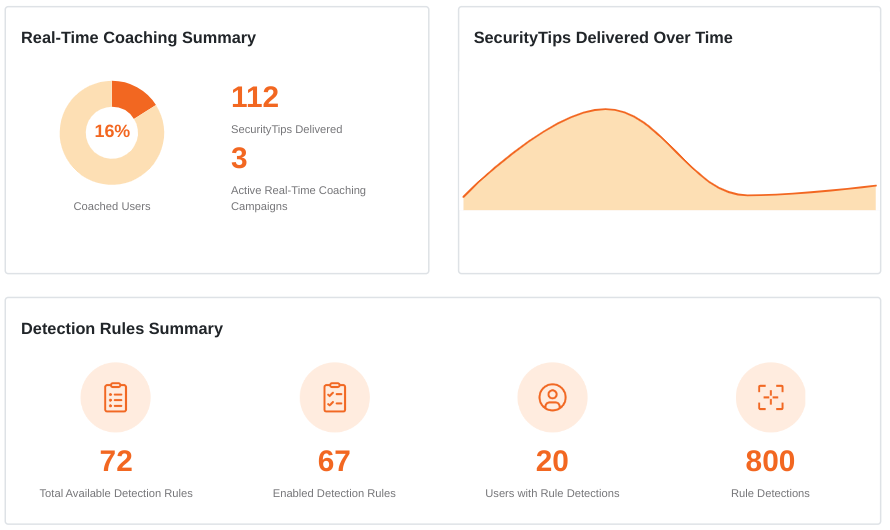
Perhaps the hardest part of training is delivering it at the right time. There is never an ideal time for employees to take time out of their day to complete their training. Which is why it’s important to not just provide the option of short and quick modules which can be completed during a tea break. But have a method to intervene with training when it is needed the most. With SecurityCoach users can be coached in real-time based on their real-world behaviours.
Whichever tool you use, make sure the training provided is relevant, timely, and appropriate to make it stick.
Find out what percentage of your employees are Phish-prone™ with our free test.